Syslog logging with Cisco ASA
By Roman Pertl
In the last week I was tweaking the logging setup of our Cisco ASA firewalls at work and find out why it didn’t work in the first place and how to disable “unneeded” messages. Again this post is nothing you won’t somewhere on the Internet or in the Cisco Documentation or by cafefully looking the ASDM interface.
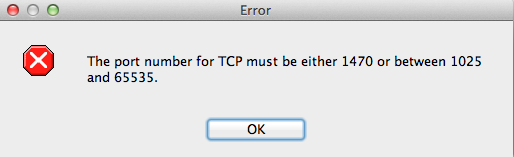
First you need to setup to which server you are want to log. The settings should be pretty straight forward. You cannot use the standard port TCP 514 with Cisco ASA, so we setup d a DNAT on the syslog server from port TCP 1470 to TCP 514. The commandline option is:
logging host interface-name syslog-ip-address proto/port
There’s an important option at the top of the page. The option allows traffic to in case the syslog servers is down (only works with TCP syslog of course). I don’t find the idea of introduction a dependency between the syslog server and the firewall a good idea (at least if you use graylog which wasn’t very stable in the past, although it has improved in the latest versions). The commandline option is:
logging permit-hostdown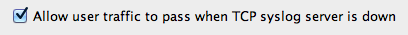
The Cisco ASA doesn’t send the hostname by default (tested on version 8.4). In order to get the Cisco ASA to send the hostname in the syslog message you need to enable the following command
logging device-id hostnameI don’t know where to find this option in the ASDM.
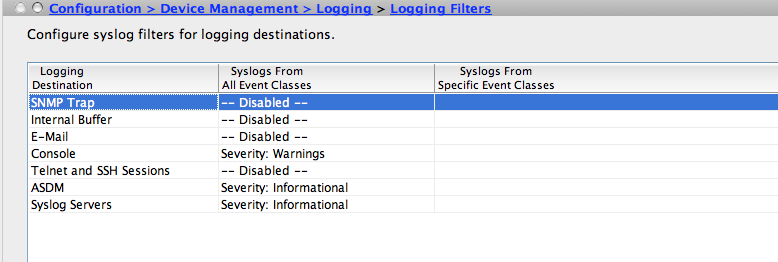
It’s not enough to configre the syslog server to get it working. You also need to enable it in the syslog filter and setup which syslog levels you want to log to syslog, via email etc. You can define custom map of filters based on event class and severity or just filter on serverty. I find the level informative to be the best one if you disable some messages which produce a lot of messages in the next step. It is crucial to have syslog not disabled on this page, otherwise there will be no logging to your syslog server.
The commandline options are:
logging trap informational
logging asdm informationalThe last step is do define which logging messages the ASA should log which which serverty, e.g. you can define that “syslog id” e.g. 105005:
%ASA-1-105005: (Primary) Lost Failover communications with mate on interface interface_name.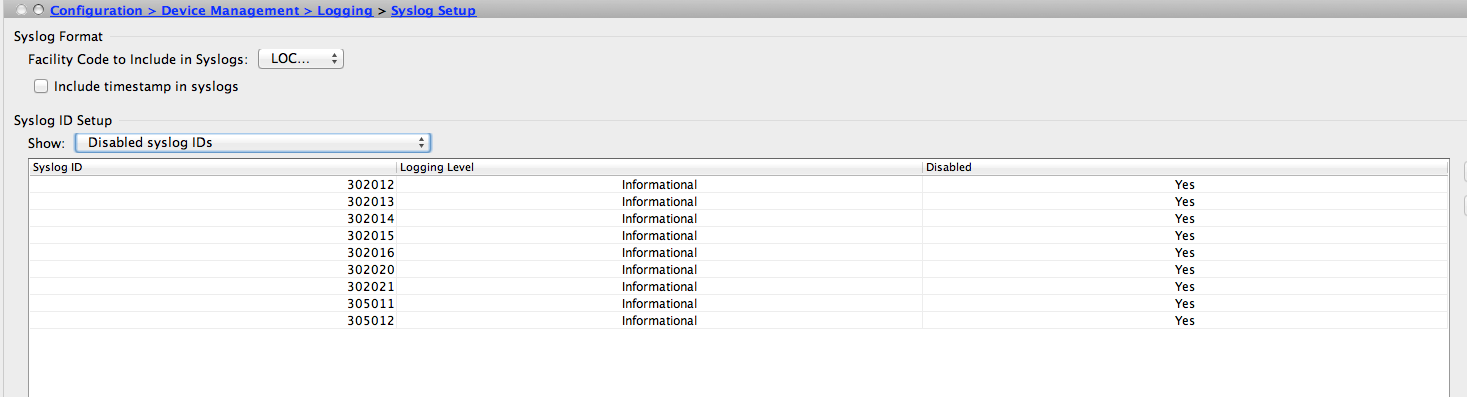
I have found that the connection tracking is very “informative” and logs each connection creation and teardown despite if you enable or disable logging of the firewall rule. So I disabled these “syslog ids” in order to have a readable logfiles. This setting also applies to the logging window you can open in the ASDM.
You can also disable those “syslog id” in the commandline:
no logging message 305012
no logging message 305011
no logging message 305012
no logging message 302012
no logging message 302013
no logging message 302014
no logging message 302015
no logging message 302016
no logging message 302020
no logging message 302021The option “log timestamps” sounds good, but we had problems with this option on our central syslog server server (graylog2). After enabling the option graylog could not correctly parse the syslog message and wouldn’t log the message with the correct hostname.
So now we have a working syslog setup wich our ASAs which only contain the syslog message we would like to have.